Tag: Security
-
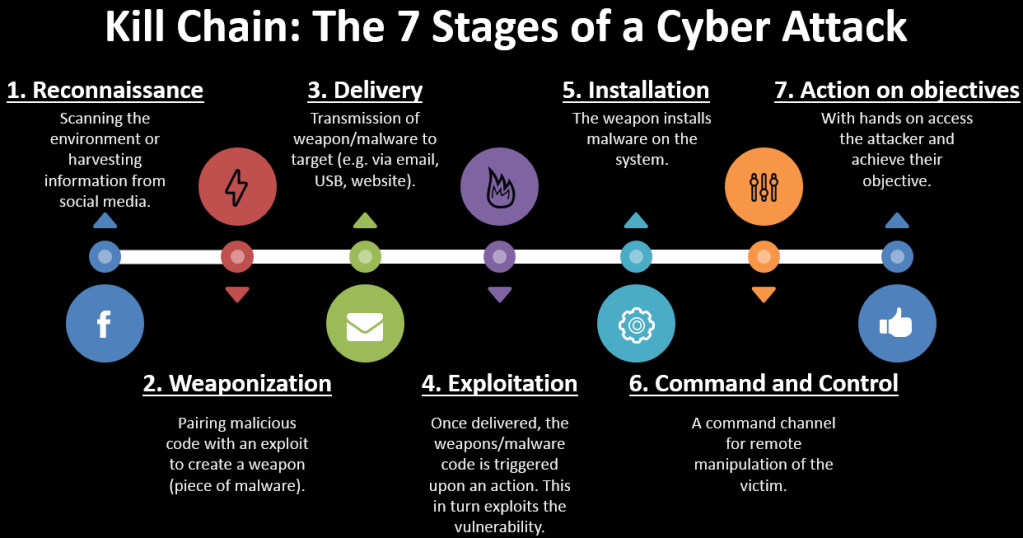
Kill Chain: The 7 Stages of a Cyberattack
Originally published in the Thomson Reuters Tax & Accounting Blog By Joseph Raczynski In our new world reality where cyberattacks are a daily occurrence and every organization must focus on critical infrastructure surrounding cybersecurity, businesses have begun to think like the military. How can we defend our enterprise? To that end, it’s not surprising that companies…
-

Podcast: The Legal Implications of Driverless Car Technology with Akerman’s Gail Gottehrer (Part 2)
Originally published in the Legal Executive Institute. By Joseph Raczynski, Gregg Wirth, and Gail Gottehrer In a new two-part Thomson Reuters’ Legal Executive Institute podcast, Joe Raczynski, Legal Technologist and Futurist with Thomson Reuters Legal, discusses the hot topic of driverless car technology and its impact on the legal industry with attorney Gail Gottehrer, partner…
-

Cybersecurity Trends and The Dark Web in Legal (VBlog)
By Joseph Raczynski The latest video on Cybersecurity as it relates to the Legal industry. This was recorded for Thomson Reuters across all business units.
-

How prepared are law firms to face cyber security threats?
By Joseph Raczynski The hacking of Panamanian law firm Mossack Fonseca last April resulted in 11.5 million leaked attorney-client privileged documents, exposing the widespread use of off-shore businesses by wealthy individuals and corporations around the world and highlighting the imperative need for proactive measures against corruption and other illicit financial activity. But what it also…
-

Google Glass – Thoughts on Glass: Privacy, Security and Its Future
By Joseph Raczynski This is part two in a series of video’s surrounding Google Glass. This is the Privacy, Security and future of Google Glass. In this video we get to see the complete Google Glass. Take a look at the Google Glass Explorer program. Glass Series Includes: 1) Glass Unboxing 2) Thoughts on Glass:…

